Our Capabilities
Proven Expertise to Prevent, Prepare for, and Protect Against Cyber Threats
We Specialize in Cyberscurity to Protect Your Business
Advisory
Our team offers expert guidance to align your security posture with evolving threats and business goals.
Strategic Security Planning
Our team can advise on creating a comprehensive security roadmap tailored to your organization’s needs, ensuring alignment with both current challenges and long-term growth objectives.
Risk Assessment & Compliance Guidance
We provide thorough evaluations of your security vulnerabilities and provide guidance on the best assessment schedule and the most impactful types of assessments to ensure ongoing security and compliance with internal, industry, and client requirements. Anchor is known for providing Security Assessment services that are comprehensive, accurate, and exceptionally detailed.
Executive Advisory Support
Our Virtual Chief Information Security Officer (vCISO) service offers ongoing advisory support, giving you executive-level strategic direction without needing a full-time hire.
Policy Development & Governance Recommendations
We guide you through establishing and refining security policies, frameworks, and governance strategies that enhance your overall cybersecurity resilience.


Integration
We leverage our teams’ technical expertise to enhance your IT capabilities, from installation to configuration and ongoing support.
Expert Engineering Capability
Our team brings a wealth of industry-specific experience, enabling us to adapt integration solutions to meet the unique technical needs of any organization.
Comprehensive Integration Expertise
We focus on the practical implementation of security controls across different environments, leveraging our technical skills to ensure deployments are effective. Our expertise encompasses working in complex scenarios, including environments with zero downtime requirements and strict regulatory standards, ensuring each integration is carried out with precision, resilience, and adherence to compliance.
Deployment & Optimization of Security Solutions
Our integration capabilities ensure that security solutions are deployed efficiently and optimized for peak performance. We leverage best practices for configuration and customization to align with your specific business and technical requirements.
Security Control Validation
We thoroughly assess and validate technical security controls to ensure they are effectively implemented and align with your security objectives. We focus on evaluating control completeness, appropriateness, and overall performance across multiple critical dimensions.
Technology Procurement
As a Value-Added Reseller (VAR), we help organizations acquire the right cybersecurity tools and solutions for optimal protection and performance. Through our extensive network of partners, we provide access to a wide range of security technologies and advocate on your behalf to secure the best possible deal.
Network Infrastructure
Network Design & Deployment
Firewall Implementation & Management
Remote Access
Network Access Control (NAC)
Visibility Solutions
Managed Detection & Response (MDR)
Vulnerability Management
Security Information and Event Management (SIEM)
Managed Threat Monitoring
Endpoint Control
Endpoint Detection & Response (EDR)
Application Whitelisting
Encryption
Patch Management
Identity & Access Management (IAM)
Security Platforms
Security Gateways
Security Management
Endpoint Protection Platforms (EPP)
Unified Threat Management (UTM)
Risk Management
We’re experts at identifying, managing, and remediating cyber risk. We levereage a deep understanding of cyber risk, comprehensive risk assessments, and our myCYPR risk manaement platform to provide greater risk visibility and continuous risk oversight for your organization.
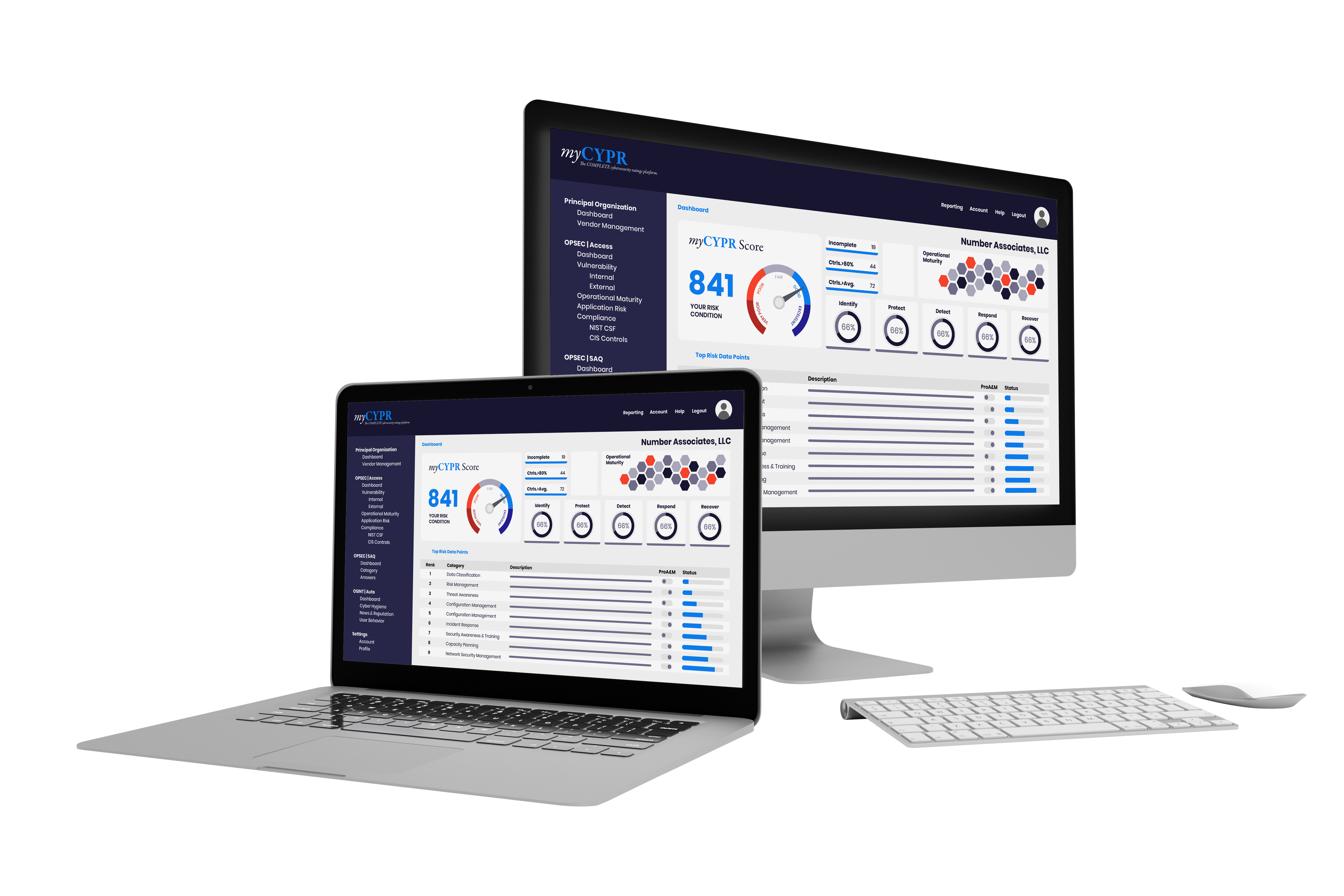
myCYPR | Risk Management Platform
myCYPR is our dedicated risk management platform designed to help organizations gain visibility into their risk landscape. With myCYPR, you can track, manage, and mitigate both internal and third-party risks. The platform integrates core risk management tasks into a streamlined tool, covering assessments, questionnaires, compliance tracking, and remediation insights to help your organization make proactive, risk-informed business decisions.
Visit myCYPR.com for a full overview of features, benefits, and use cases.
Risk Assessment Expertise
Our capabilities cover both internal and third-party risks, helping organizations identify vulnerabilities, assess their risk landscape, and take proactive steps to mitigate potential threats. We can evaluate both internal operations and third-party vendors to identify security gaps, mitigate risks, and secure your entire network.
Risk-Based Security Planning
We focus on prioritizing and aligning security initiatives based on your organization’s unique risk profile, ensuring resources are effectively allocated to areas of greatest impact.
Incident Response Strategy
We advise on building and maintaining incident response plans that prepare your organization to handle an incident from the moment a breach is confirmed. When every second counts, you’ll have the preparation and clear actions needed to minimize impact effectively. Our Incident Response services provide your organization with comprehensive coverage, from planning and preparation to forensic investigation and response.
Compliance Alignment
We help identify compliance gaps and provide guidance to ensure adherence to regulatory requirements, mitigating risks associated with non-compliance.
Continuous Risk Monitoring & Improvement
By implementing real-time monitoring tools and ongoing evaluations, we ensure that emerging threats are detected early and risk mitigation strategies are adjusted accordingly. This continuous cycle of monitoring, assessment, and improvement allows your organization to stay proactive and resilient against an evolving threat landscape.
Take control of Cyber Your Risk
Cybersecurity is a continuous journey. Our tailored security services and risk assessments help you define a robust strategy, identify vulnerabilities, and take control of your cyber risk effectively. We’re eager to ensure your business stays ahead of emerging threats and remains secure.
